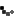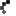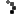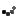Syed Farook, 28, and Tashfeen Malik, 27, the suspects responsible for the San Bernardino Islamic terror attack. (Photos: AP/EPA)
One inevitable sequel to a terrorist attack is seeing the ugly mugs of creeps-turned-monsters thrust before us over a multitude of news cycles. Another is a debate over cellphone encryption.
Encryption is a means of turning information into secret code. Terrorists communicate through encrypted devices to hide their plans and protect the identities of their co-conspirators. For obvious reasons, law enforcement wants to know what’s being said and to whom.
The FBI had been demanding that Apple turn over an encryption key to crack the iPhone used by San Bernardino gunman Syed Rizwan Farook. Apple has refused, arguing that helping the FBI hack Farook’s iPhone would put the privacy of other iPhone users in jeopardy. That would be bad for business.
Apple’s case has always been morally and legally flawed, but now it may be moot. That’s because on the very day of the terrorist outrage in Brussels, the Justice Department announced it may now be able to get at the information in Farook’s iPhone without Apple’s input.
An unidentified third party has reportedly found a way to hack the phone. That method is being tested to ensure that it doesn’t destroy the valuable data in the process.
If it succeeds, Apple will have lost in three ways. No. 1: Consumers are no longer assured that iPhone data is invulnerable. No. 2: By forcing others to find a means of cracking an iPhone, Apple loses control over the process. And No. 3: Apple is left with having fought the bad fight.
All that goodwill Apple has amassed for its wonderful products could start draining away as Americans wonder what side it’s on. The rampage in San Bernardino took 14 lives and grievously injured 22 others. Survivors and relatives of the dead have protested Apple’s defense of a mass murderer’s cellphone data. That’s definitely bad for business.
Suppose Belgian investigators cleaning up the body parts came across an encrypted iPhone of a terrorist impressed by Apple’s promise of privacy. Would Apple refuse to help uncover accomplices in that bloodbath, as well?
Some argue that Farook’s iPhone 5c is easier to crack than the newer iPhones. Does Apple now want to bet that hacking the iPhone 6 or a later model can’t be done by a highly talented geek?
The Justice Department’s legal basis for requiring Apple to unlock an encrypted device is the 1789 All Writs Act. The law applies only if compliance is not an unreasonable burden. Apple claims invading Farook’s iPhone would be “unreasonably burdensome.”
With a search warrant based on probable cause, law enforcement may barge into your home, break into your metal file cabinets and look in your underwear drawer. (For further information, consult some “Law & Order” reruns.)
One’s cellphone is not a sacred space. Mobile phone users worried that police doing a warranted search might come across their third-grader’s math scores or a prescription for Viagra should not put such data onto their gadget in the first place.
The concern in Apple’s boardroom and elsewhere in the Silicon Valley is that governments less constrained by civil liberties than ours would demand the key to breaking the encryption. They already do, but that’s between the companies and the other countries. It’s really not the American public’s problem — unless you want to argue that tech company profits trump national security.
Apple’s position was insupportable. Now it may be irrelevant. A wise move for those in the tech industry would be to quietly work out some accommodation with law enforcement in the halls of Congress. Rest assured, they won’t want to hold such discussions in the heat of another, even more devastating terrorist attack.